Source code: https://github.com/JiaoXianjun/BTLE
Verilog/FPGA implementation: https://sdr-x.github.io/open_btle_baseband_chip/
A introduction of principle how to capture and follow BTLE frequency hopping link:
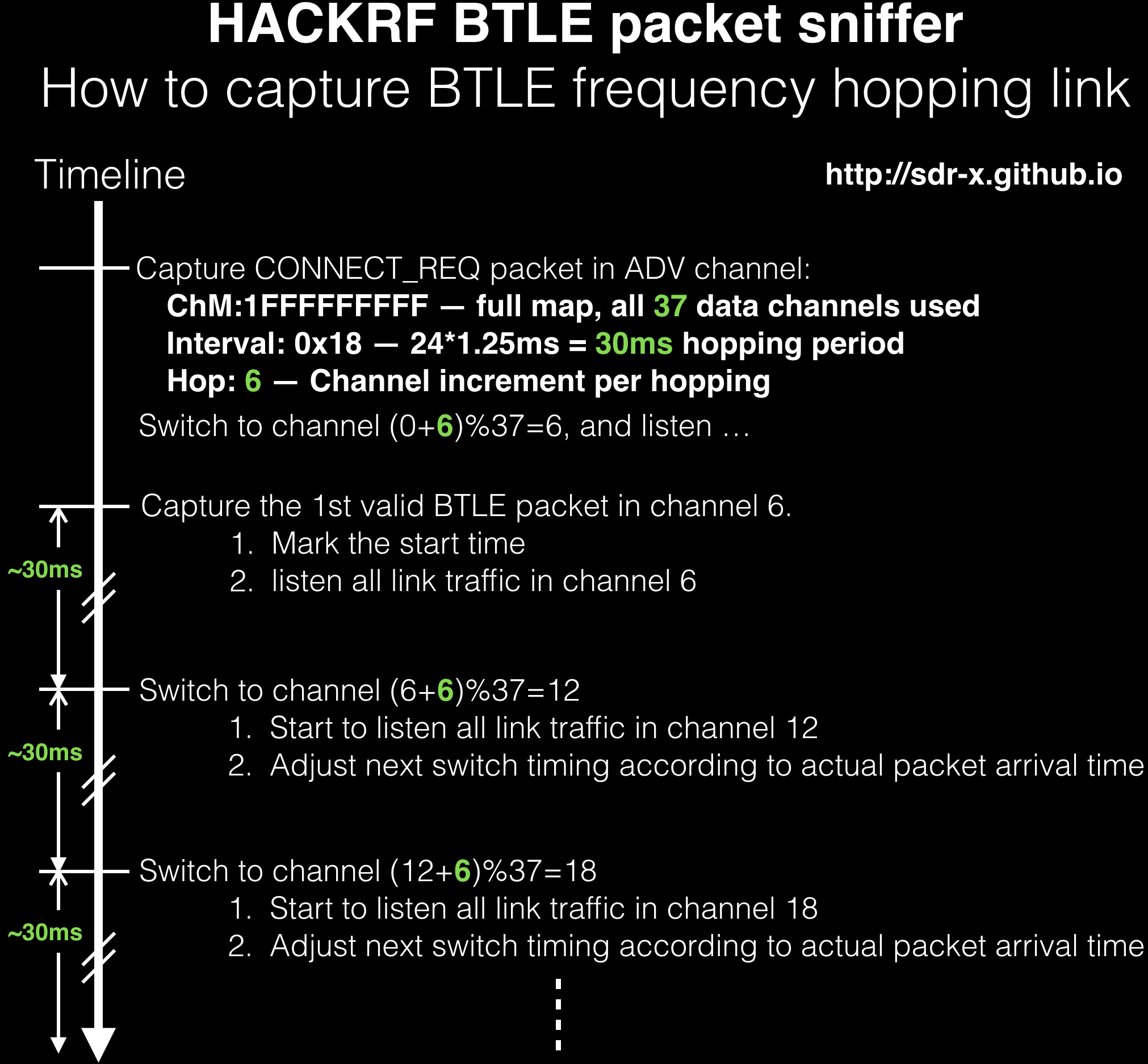
Nov. 2015: So excited that the HACKRF BTLE packet sniffer/scanner can follow hopping data channels automatically now! Just like TI’s sniffer.
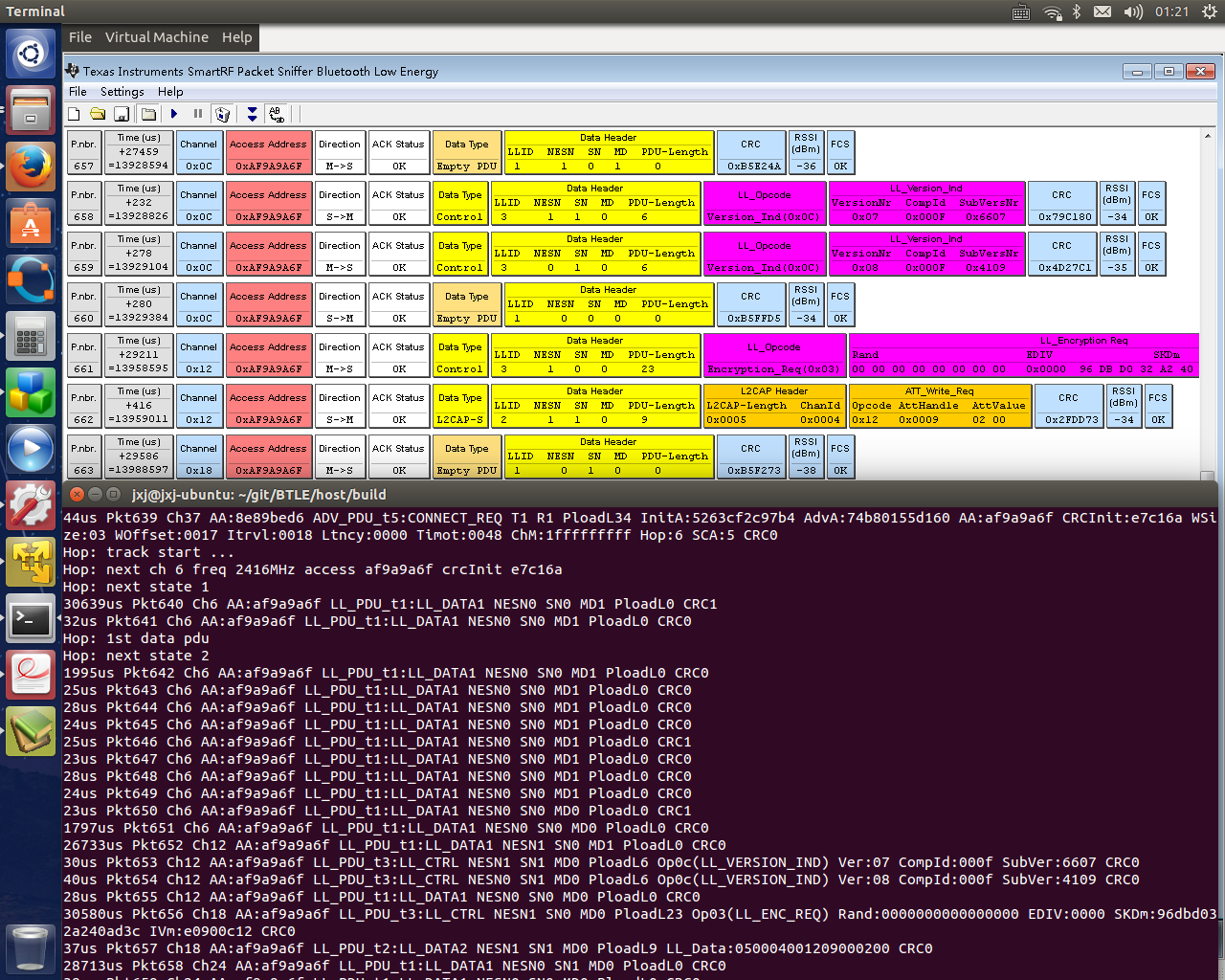
New added options:
-o –hop
This will turn on data channel tracking (frequency hopping) after link setup information is captured in ADV_CONNECT_REQ packet.
-f –freq_hz (need argument)
This frequency (Hz) will override channel setting (In case someone want to work on freq other than BTLE. More general purpose).
-m –access_mask (need argument)
========================================
This is extended from my btle_tx project
Now all BTLE channels (0~39, bothe ADV and DATA channels) are supported. You can use btle_tx and btle_rx to send or sniff on any BTLE channel.
A Raw mode is added to both btle_tx and btle_rx. Under this mode, after access addr is detected, following raw 42 bytes (without descrambling, parsing) are printed out. By this way, you can do other experiments or communication between HACKRF boards easily.
Introduction source code and usage
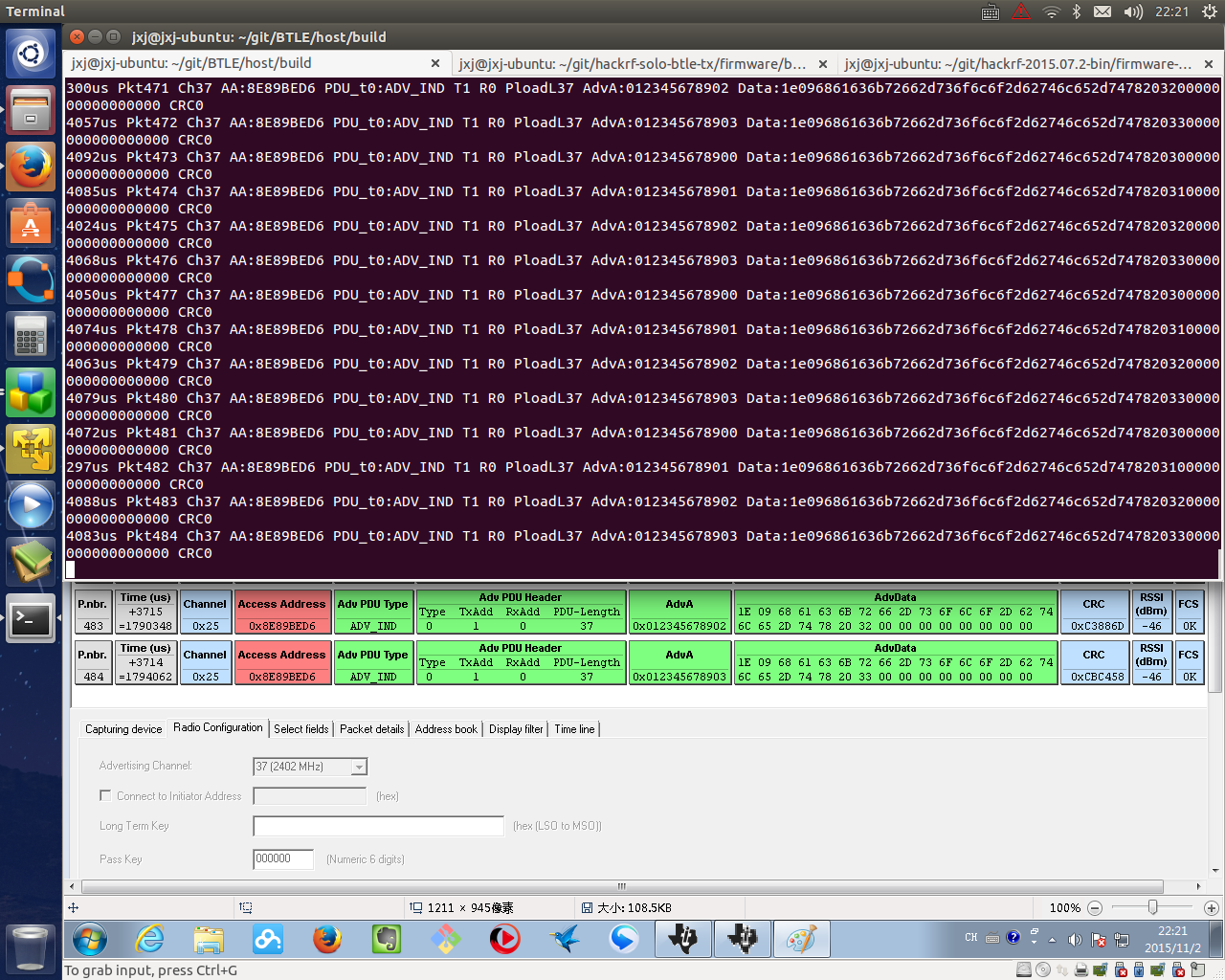
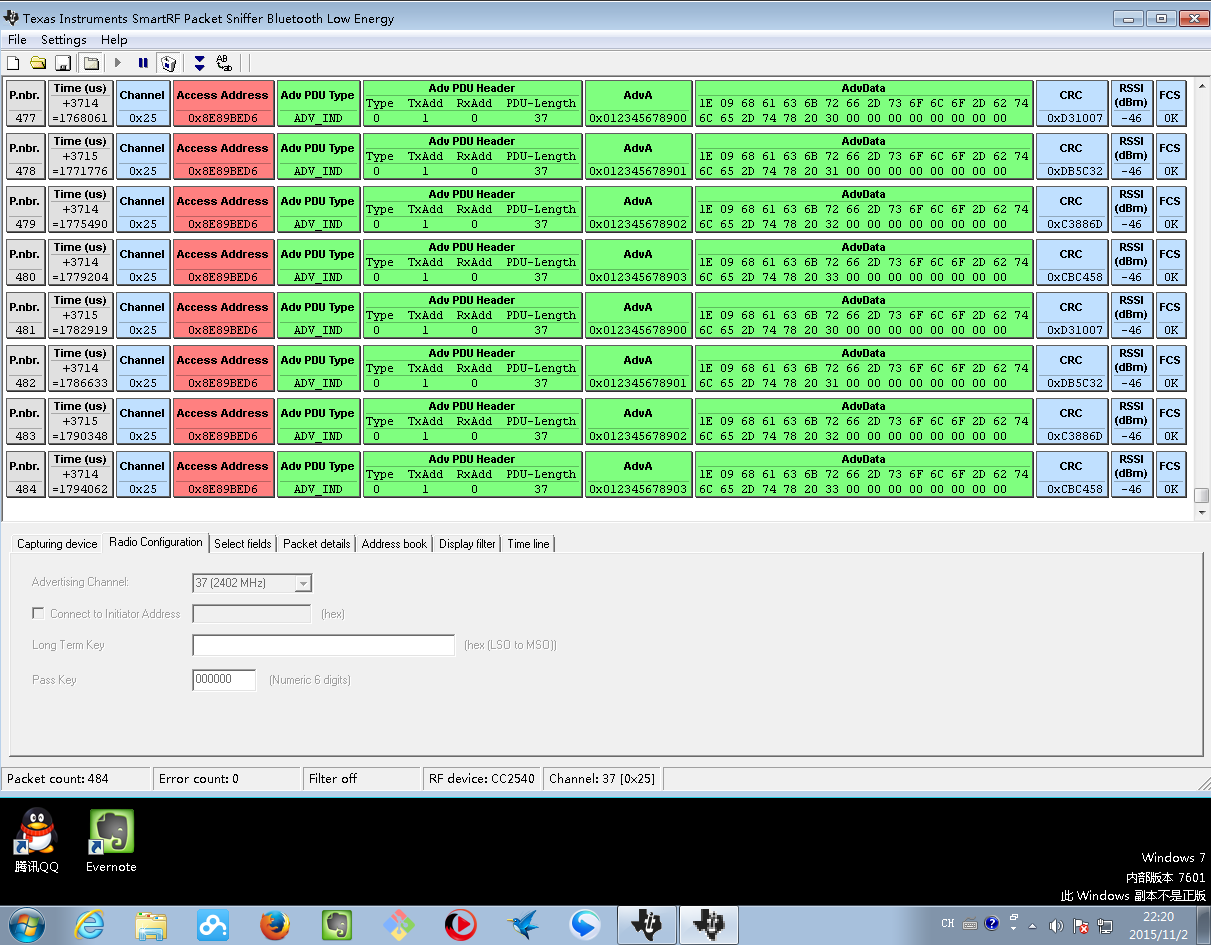
Snapshots of HACKRF BTLE packet sniffer VS TI’s packet sniffer under fastest flow of continuous/non-gap BTLE packets sequence to demonstrate full real-time processing ability. They capture the same amount of packets and contents: